Embedded Linux and IoT devices are increasingly targeted by cyber threats, making robust security measures essential. One of the most critical defenses is Secure Boot, a mechanism that ensures only trusted software runs on a device.
Originally presented in our webinar Safeguard your Embedded Linux Devices with Secure Boot, this guide explores:
- What Secure Boot is and why it matters
- How it protects against firmware and OS tampering
- Compliance with regulations like the EU Cyber Resilience Act (CRA)
- Best practices for implementation
Why Secure Boot is Essential
1. Preventing Unauthorized Modifications
A compromised bootloader or kernel can give attackers full control over a device. Secure Boot ensures that:
- Only signed and verified software executes.
- Malicious firmware or rootkits cannot persist across reboots.
2. Meeting Regulatory Requirements
The EU Cyber Resilience Act (CRA) mandates that embedded devices must:
- Protect software integrity against tampering.
- Verify authenticity of all boot components.
⚠️ Without Secure Boot, devices may fail compliance audits, risking market access.
How Secure Boot Works
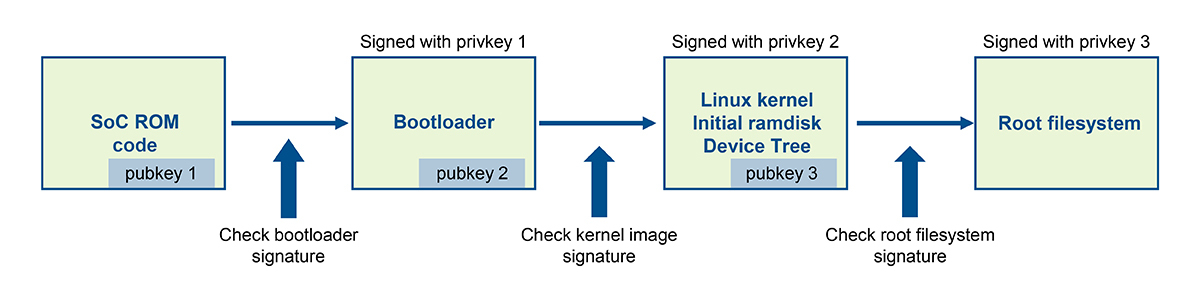
Secure Boot establishes a chain of trust, where each component validates the next before execution:
- SoC ROM Code → Checks the bootloader’s digital signature.
- Bootloader (U-Boot) → Verifies the FIT image (kernel, device tree, initramfs).
- Initramfs → Validates the root filesystem.
Key Security Guarantees
- Authenticity – Confirms software comes from a trusted source.
- Integrity – Ensures no unauthorized changes were made.
❌ What Secure Boot Doesn’t Do
- Encrypt data (requires separate disk encryption).
- Protect against runtime attacks (e.g., weak SSH passwords).
Implementing Secure Boot
1. Fusing Hardware Keys (One-Time Step)
- A public key is permanently burned into the SoC (e.g., NXP’s HAB, TI’s HSM).
- The device only boots software signed with the matching private key.
2. Building a Signed Software Stack
Each component (bootloader, kernel, rootfs) must be signed during build:
- U-Boot → Validates the kernel.
- Kernel → Checks the root filesystem (using
dm-verityorcomposefs + fs-verity).
3. Handling Secure Updates
Since locked devices reject unsigned code:
- OTA updates must be signed (Torizon uses Uptane for secure updates).
- Recovery mode may require physical access (e.g., NXP’s
uu-tool).
Key Security Guarantees
Secure Boot vs. Other Security Measures
| Feature | Secure Boot | Full-Disk Encryption | TPM-Based Security |
|---|---|---|---|
| Prevents unauthorized boot | ✅ Yes | ❌ No | ❌ No |
| Protects runtime data | ❌ No | ✅ Yes | ✅ Yes |
| Hardware dependency | SoC-specific | Flexible | Requires TPM |
Best Practice: Combine Secure Boot with encryption and runtime protections for full defense.
Secure Boot vs. Other Security Measures
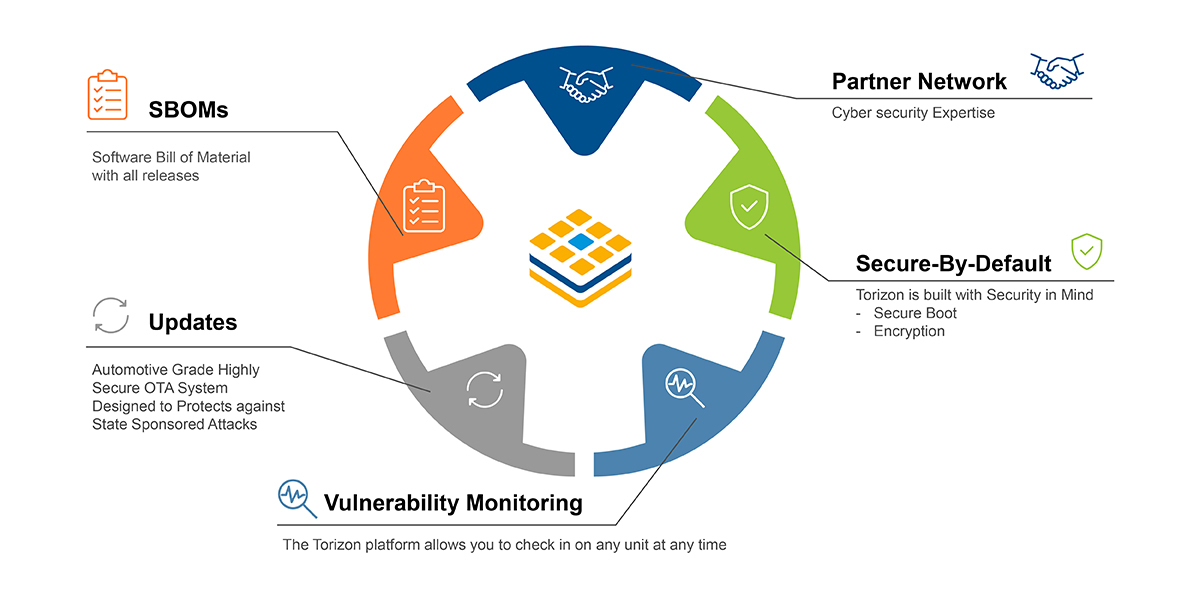
For developers, implementing Secure Boot manually can be complex. Torizon simplifies it with:
- Pre-configured Secure Boot for Toradex hardware.
- Signed OTA updates (Uptane standard).
- Automatic integrity checks (kernel, rootfs, containers).
- Compliance-ready SBOM (Software Bill of Materials).
Example Attack Prevention
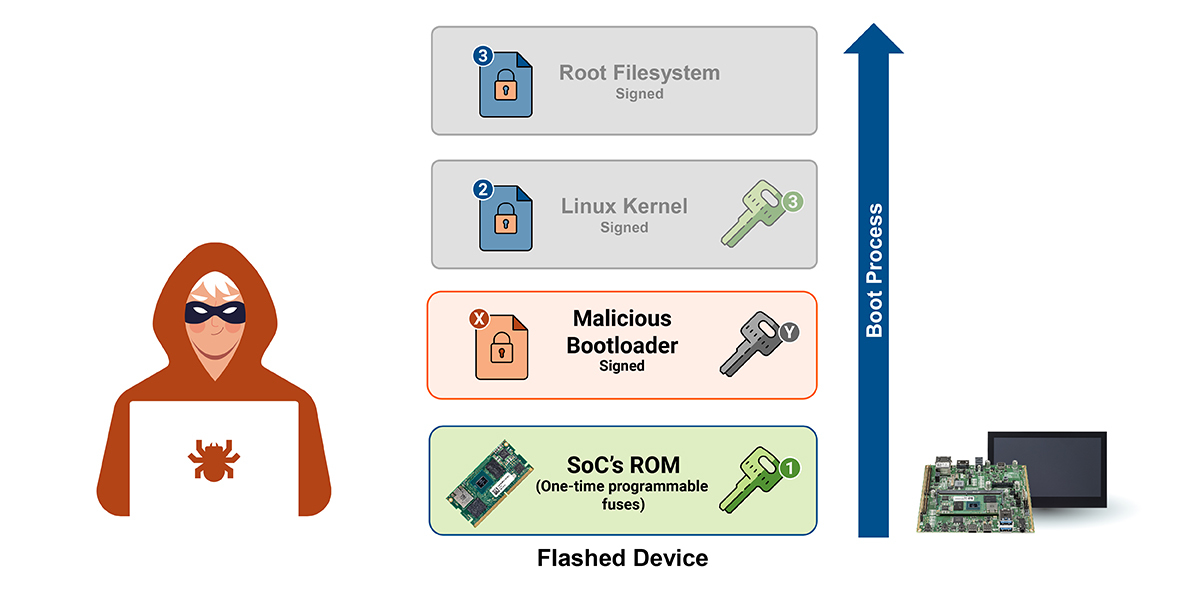
- Modified bootloader? → Device refuses to boot.
- Tampered kernel? → Boot process halts.
- Malicious rootfs update? → Get detected by SB and the boot will be halted
Building a Secure Future for Embedded Linux
Secure Boot is no longer optional—it’s a critical foundation for securing embedded Linux and IoT devices against firmware attacks, unauthorized code execution, and compliance risks. By implementing a robust chain of trust, developers can ensure their devices boot only verified software while meeting stringent regulations like the EU Cyber Resilience Act (CRA).
However, Secure Boot is just the beginning. A truly secure system requires:
- Encrypted storage to protect sensitive data.
- Secure OTA updates to patch vulnerabilities.
- Runtime monitoring to detect intrusions.
- Vulnerability scanning, secure coding practices and proper thread assessments.
Key Security Guarantees
With solutions like Torizon, developers gain an integrated approach—combining Secure Boot, trusted updates, and compliance-ready tooling. Whether you’re building industrial IoT, medical devices, or automotive systems, now is the time to prioritize security from the ground up.
- Get started today: Torizon Secure Boot Documentation
- Join the discussion: Toradex Community Forum
The future of embedded systems is secure—make sure your devices are ready.