Introduction
Time flies.
Sometimes, it seems that someone boosts the time ticker variable on Life's loop. And when you notice it, the ++year is executed and here we are almost in 2025.
And with it comes the EU Cyber Resilience Act (CRA), an upcoming European Union Regulation whose goal is to increase the cybersecurity of new products.
Luckily, Torizon has several security features that help you reach compliance with reduced effort and cost.
Secure Boot is one of the pieces of the puzzle to becoming compliant, as it ensures only trusted software is executed during the boot. The ability to update a device in the field is another piece that allows deploying security fixes to software vulnerabilities throughout the software stack. How do we connect them so both coexist? Through the security hardening of U-Boot.
U-Boot is the bootloader used in Toradex System on Modules. This software is responsible for loading the Linux kernel into memory and handing over the system execution.
This blog is heavily inspired by the Toradex Developer Website article on Security Hardening of U-Boot, written by my colleague Rogerio Guerra Borin, one of the lead engineers behind the Toradex Secure Boot implementation.
Why Hardening?
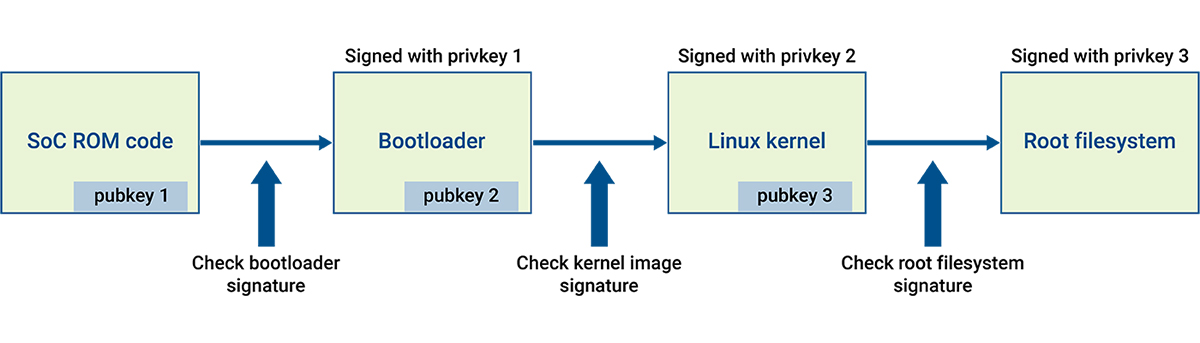
The Toradex Secure Boot implements a Chain of Trust, where the current stage of the boot process validates the next stage until the system is booted.
The security hardening of U-Boot is a measure that protects what we refer to as the second link in the Toradex Secure Boot Chain of Trust. This is the step of the process where the Linux Kernel is loaded and executed by U-Boot:
The Torizon OS is a production-ready Linux distro capable of updating all system components, including the OS and the bootloader. Unlike other approaches where all required data is hardcoded in the bootloader, in this case, some artifacts are kept in a storage device to make these system updates and rollback possible.
If not properly protected, those artifacts may be used by attackers to tamper with the boot process and possibly run untrusted software. Therefore, the security hardening of U-Boot ensures that it is only possible to boot a signed kernel, even if the artifacts are tampered with.
What is Hardening?
In the context of the Toradex Secure Boot, U-Boot hardening is a series of modifications that intend to:
- Prevent execution of unsigned software: only authentic and trustworthy software can be executed by U-Boot.
- Prevent modification to the running software: U-Boot must not be allowed to modify itself.
- Prevent injection of kernel arguments: only authentic and trustworthy arguments can be passed from U-Boot to the Linux Kernel.
These measures protect the system from attackers under some circumstances:
- Physical or remote root access to the Linux shell.
- Physical access to the U-Boot Command Line Interface.
- Physical access and modification of the flash storage content.
How is U-Boot Hardened?
To protect the second link of the Chain of Trust, we take the following measures:
- Command whitelisting: block commands that make it possible to run unsigned code or modify U-Boot itself.
- Exclusive signed software execution: prevent unblocked commands from running unsigned software.
- Self-overwriting protection: prevent U-Boot commands from writing to the memory region where U-Boot itself is loaded.
- CLI access prevention: optionally disables the U-Boot CLI to help improve security by eliminating an attack vector.
- Kernel command-line protection: prevents changes to the variable that keeps the arguments passed to the Linux Kernel.
To learn more about these, I recommend reading the Toradex Developer Website article on Security Hardening of U-Boot.
Conclusion
Given the above quick peek into the Toradex Secure Boot implementation, adopted by the Torizon OS, I expect you were able to understand our approach to making your device secure while loading software during boot, capable of receiving secure remote updates, and ready for the EU Cyber Resilience Act.
References
EU Cyber Resilience Act:
Torizon:
Toradex Secure Boot: