Einhaltung der Sicherheitsvorschriften
Torizon senkt den Aufwand und die Kosten für die Einhaltung von Vorschriften und sorgt dafür, dass Sie sich auf den einzigartigen Wert Ihrer Produkte konzentrieren können, anstatt sich mit dem Abhaken von Kästchen in den Richtlinien für Sicherheitsanforderungen zu beschäftigen.
EU Cyber Resilience Act (CRA)
Das neu vorgeschlagene EU Cyber Resiliance Act ist für das industrielle Internet der Dinge (IIoT), industrielle Automatisierungs- und Steuerungssysteme und Allzweck-Mikroprozessoren von großer Bedeutung. Hintergrund sind die enormen Kosten, die durch Cyberkriminalität verursacht werden und die für das Jahr 2021 auf 5,5 Billionen EUR geschätzt werden. Die EU geht davon aus, dass dies auf niedrige Cybersicherheitsstandards in Hard- und Software und die Unfähigkeit der Nutzer zurückzuführen ist, aufgrund fehlender Transparenz Produkte mit angemessener Sicherheit auszuwählen. Die Strafen für die Nichteinhaltung der Vorschriften belaufen sich auf bis zu 15 Millionen Euro oder 2,5 Prozent des weltweiten Jahresumsatzes.
Einige der Anforderungen des Cyber Resiliance Act
- Kommunikation über Schwachstellen
- Keine Verzögerung bei der Behebung der Sicherheitslücken
- Sichere standardmäßige Konfiguration
- Risikobewertung der Cybersicherheit
- Anforderungen an die Software-Stückliste (SBOM)
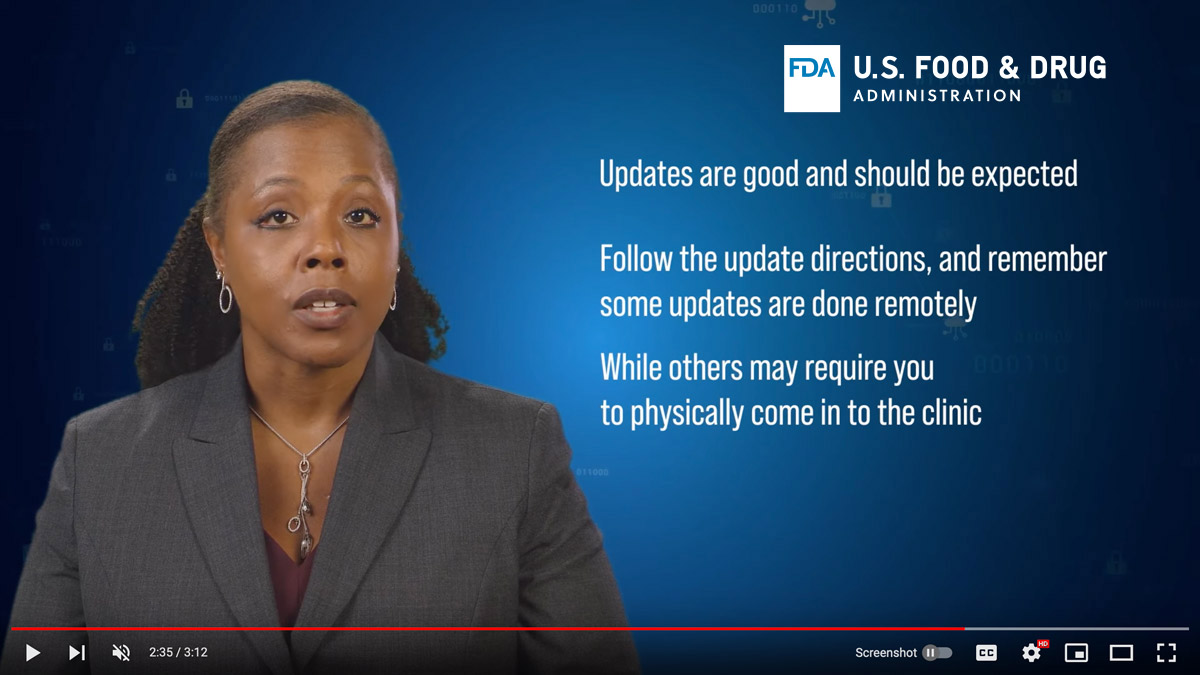
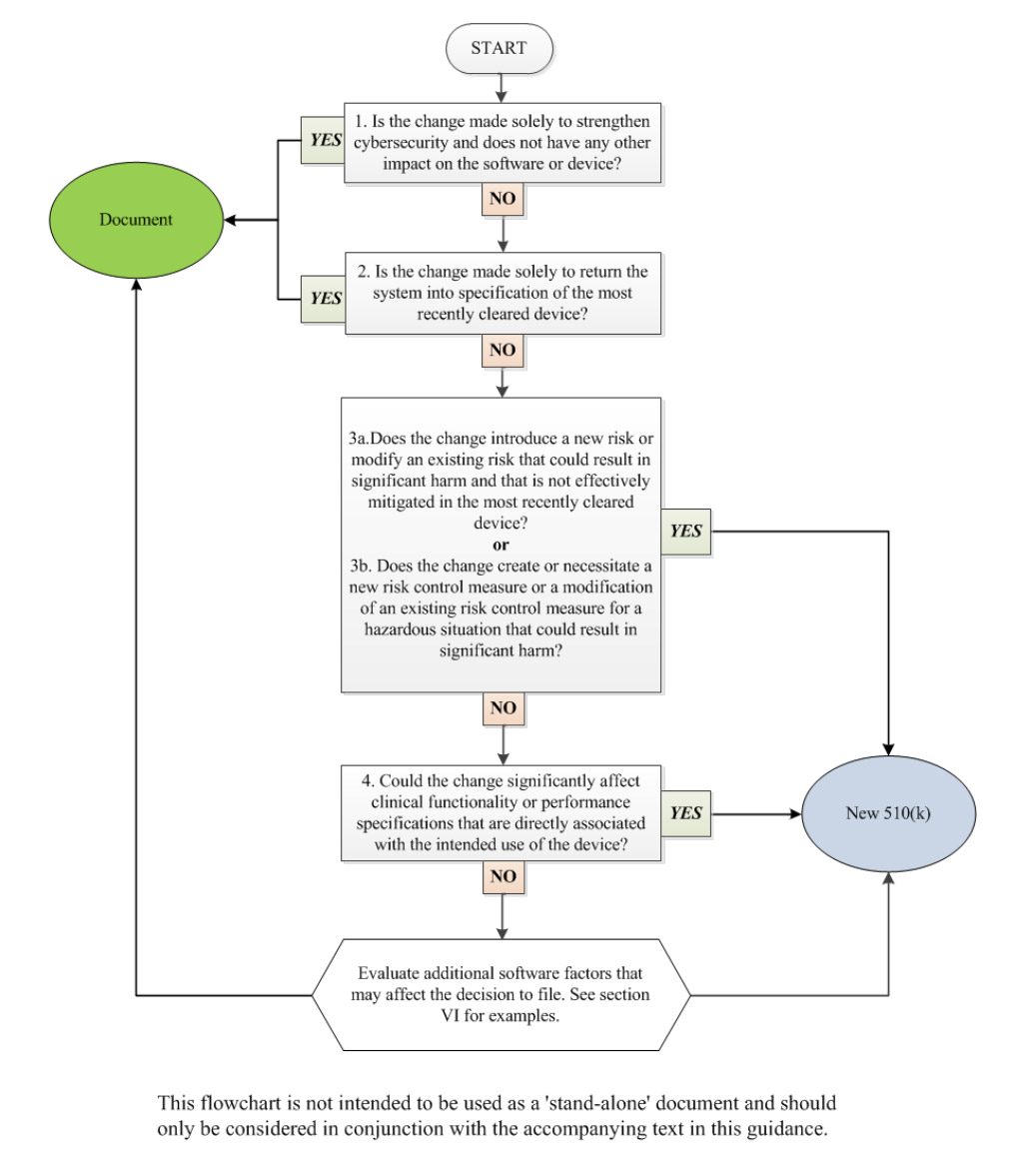
FDA- Software-Updates werden erwartet
Lange Zeit haben die Hersteller von Medizinprodukten versucht, Änderungen am HW- oder SW-Produkt zu vermeiden, um eine Neuzertifizierung und die Einreichung einer 510(k)-Meldung zu vermeiden. Die Anforderungen ändern sich jedoch. Jetzt ist es erforderlich, die Software auf dem neuesten Stand zu halten und eine sichere Aktualisierungsfunktion bereitzustellen. Nur die Verbesserung der Cybersicherheit des Geräts erfordert keine 510(k).
Die FDA hat einen neuen Richtlinienentwurf mit dem Titel Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions. Hier sind einige Punkte über Software-Updates
- Antizipieren Sie den Bedarf an Software-Patches
- Berücksichtigen Sie die Zuverlässigkeit des Aktualisierungsprozesses im Falle einer Unterbrechung oder eines Ausfalls der Kommunikation.
- Implementierung von Verfahren zur schnellen Überprüfung, Validierung und Verteilung von Patches und Updates
Whitepaper
Cybersecurity in Medical | Healthcare Devices - Evolving Regulations
Wie Torizon hilft
Zuverlässiger Aktualisierungsprozess
Bewährter Sicherheitsrahmen
Häufige OS-Updates
Schnelle Entwicklung, Prüfung und Bereitstellung
Integration mit Secure Boot (demnächst verfügbar)
Vulnerability Manager
Software-Stückliste (SBOM)
Defense in Depth
Videos
How TI and Toradex streamline cybersecurity, usability and time to market
Discover how the partnership between Toradex and Texas Instruments (TI) boosts embedded Linux security and supports compliance with the EU Cyber Resilience Act (CRA) and the FDA cybersecurity guidance . Learn how Torizon OS enables secure, efficient development on Toradex SoMs like the Verdin AM62 and Aquila AM69, and how TI integrates Torizon OS into AM62x, AM62P, and AM67 BeagleY-AI starter kits, with broader support coming soon.
Out-Of-The-Box Secure Boot and Support with Torizon
Torizon now supports Raspberry Pi, generic x86, RISC-V, and many other platforms, providing more flexibility and options for developers! Discover how Torizon is leading the way with secure boot support on the Texas Instruments AM62 System on Module and what's next on the roadmap for enhanced security features.
Cybersecurity Compliance with Savoir-faire Linux and Torizon
Discover how Savoir-faire Linux is leveraging Torizon to facilitate secure boot, manage software vulnerabilities, and support a comprehensive Software Bill Of Materials (SBOM) to enhance security from the ground up for customers.
Blog-Serie zur IoT-Sicherheit
Teil 3
Sicherheit von Software-Updates: Häufige Fehler
Dies ist Teil 3 unserer 7-teiligen Serie über Over-the-Air-Software-Updates. In Teil 1 haben wir Ihnen alle Gründe genannt, warum es wichtig ist, Software-Updates aus der Ferne bereitzustellen, und in Teil 2 haben wir über alle Gründe geschrieben, warum Software-Update-Systeme gefährlich sind. Heute befassen wir uns mit Möglichkeiten zum Schutz Ihres Softwareaktualisierungssystems, die auf den ersten Blick sicher erscheinen mögen, es aber nicht sind - mit berühmten Fehlern aus der Praxis für jedes Beispiel.
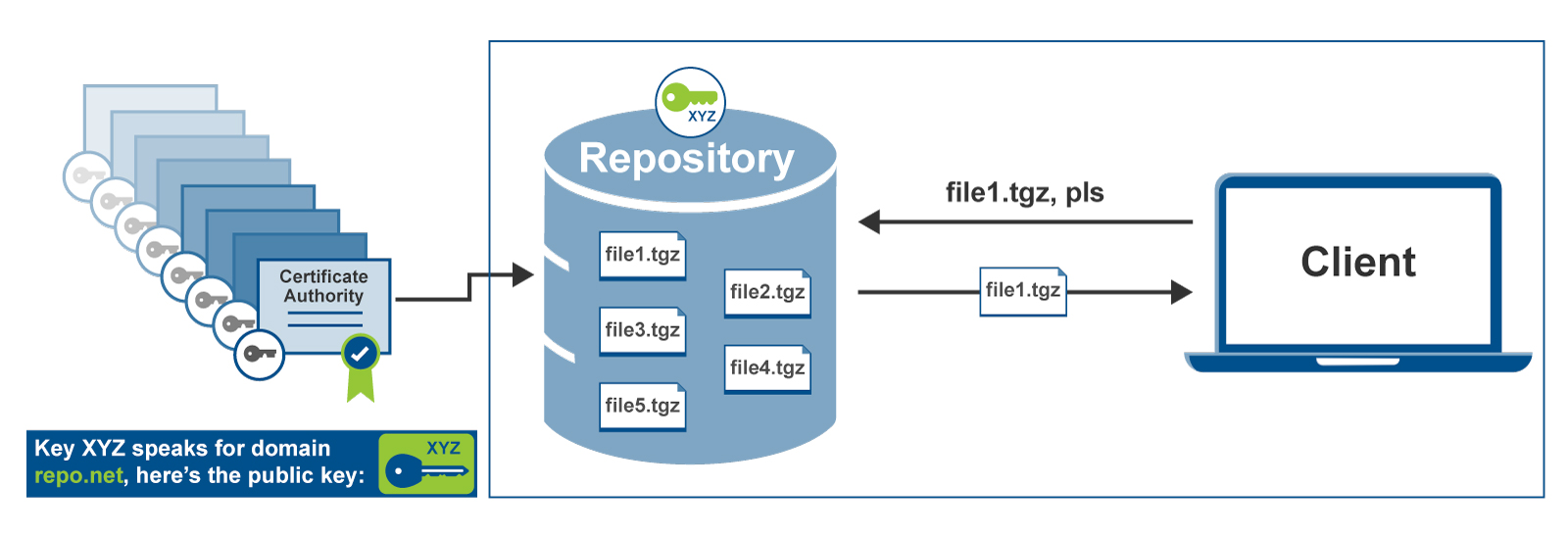
Teil 2:
Die Gefahren von Remote-Updates
Dies ist Teil 2 unserer 7-teiligen Serie über Over-the-Air-Software-Updates. In Teil 1 haben wir Ihnen alle Gründe genannt, warum es wichtig ist, Software-Updates aus der Ferne bereitstellen zu können - in der heutigen Welt können Sie kein verbundenes Gerät sicher halten, wenn Sie es nicht aktualisieren können. Der heutige Beitrag geht jedoch in die entgegengesetzte Richtung: Wir werden uns ansehen, warum Softwareaktualisierungssysteme unglaublich gefährlich sein können und warum Sie sie mit Skepsis und Vorsicht behandeln sollten.
Teil 1:
Warum brauchen wir Remote-Updates für verbundene Geräte?
Mit der explosionsartigen Zunahme der mit dem Internet verbundenen Geräte in den letzten Jahren hat sich in der gesamten Branche die Erkenntnis durchgesetzt, dass diese Geräte während ihrer gesamten Lebensdauer aktualisiert werden müssen. Dies ist der erste Teil einer Serie, die sich mit dem Konzept der Remote-Over-the-Air (OTA)-Updates befasst und den Entwicklern die Details liefert, die sie für die Implementierung von Remote-OTA-Update-Lösungen in ihre Systeme benötigen. Wir werden uns insbesondere auf die wichtigen Sicherheitsaspekte konzentrieren. Wir beginnen mit den Grundlagen.
On-Demand Webinare
Safeguard your Embedded Linux devices with Secure Boot
In this webinar, we will explain what Secure Boot is, why it’s needed, and how it’s implemented. We also present a live demo, illustrating how Toradex makes it easy to enable Secure Boot using the Yocto-based Linux Torizon OS.
Enhanced Cybersecurity and FIPS 140-2 Compliance using NXP® i.MX 8X
The road to cybersecurity compliance for regulated applications in the utilities, medical, and defense industries can be difficult. Achieving the required certifications can significantly increase timelines for development time/cost which can significantly delay a product launch.
Los geht's
Meinem Team gehören
Torizon ist vollständig in die Toradex-Hardware integriert
Torizon OS läuft auf den meisten unserer neueren Module! Nutzen Sie einen vollständig integrierten Stack und beginnen Sie noch heute mit der Entwicklung.

Die Integration von Torizon ist einfacher als Sie denken!
Torizon OS ist vollständig Open Source! Wir geben Ihnen Referenze, wie Sie es in Ihre eigene Hardware integrieren können. Machen Sie es selbst oder ziehen Sie unsere Partner zu Rate!

Alles, was Sie für den Einstieg brauchen
Um Ihre Evaluierung zu starten, wählen Sie eines der Starter Kits und profitieren Sie von der engen Software-Hardware-Integration.
Nehmen Sie Kontakt mit uns auf
Möchten Sie mehr über Torizon erfahren?